The government has announced that all government bodies using GCSX email addresses need to replace these with a government domain like gov.uk, gov.scot or gov.wales by March 2019.
They have created a blueprint which outlines how every government organisation should secure their email in future, so that information is sent securely between departments. This will be done primarily through encryption and anti-spoofing.
Encryption methods for government email
Encryption mitigates threats to email security and protects the data contained within the email. Government encryption is achieved through a process called transport layer security (TLS).
Transport layer security (TLS)
For cloud or internet-based email service, encryption is done through Transport Layer Security (TLS). It is a process of encryption which protects data while it is in transit between two computers.
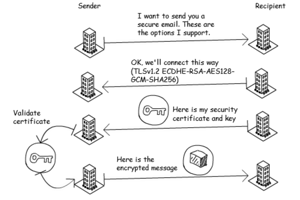
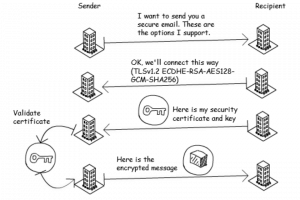
The two computers ‘agree’ to encrypt the data being sent in a way that they can both understand. If it is not encrypted in a recognised way, the recipient computer can ‘refuse’ to connect.
Establishing how the data will be encrypted happens in an email exchange. The sending server ‘asks’ the receiving server to accept a TLS connection, and shares a list of protocols for the recipient to choose from. The receiving server then sends back their chosen security certificate and public encryption key.
The sending server then confirms the security certificate, encrypts the email using the public key and sends it to the recipient. The recipient has the private key to decrypt the email. The message is sent totally securely and only the recipient can decrypt it.
This is a vital step in securing email.
If an encrypted connection can’t be established, in most cases the email will be sent unencrypted. But for government bodies, this isn’t appropriate. Both parties should insist that a TLS connection is used. Here's a diagram showing how TLS works:
Anti-spoofing
Anti-spoofing is another element of email security which makes sure emails come from the place they say they are coming from. It does this through a few processes: DMARC, SPF and DKIM/.
Sender policy framework (SPF)
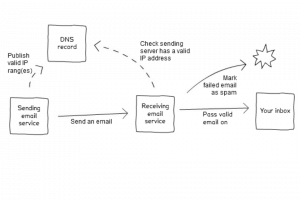
Sender policy framework validates the domain an email was sent from. It does this by listing valid sending IP addresses or domains in the DNS record. The recipient can then check if an email came from a valid IP or domain. If it didn’t it can be marked as spam.
Create and manage DKIM
DKIM stands for Domain Keys Identified Mail. DKIM verifies the domain an email came from and shows an email hasn’t been tampered with in transit. With DKIM, the recipient can filter out any emails that fail the DKIM check, which ensures any email they receive is safe to open.
To do this, DKIM uses both public and private keys.
Any email service that doesn’t check for DKIM signatures will let through every email.
Organisations can create a rule that users must look for messages that fail the DKIM check and mark any that do as spam. Any email service that doesn’t check for DKIM signatures will let through every email.
Domain-based Message Authentication, Reporting and Conformance (DMARC)
Phishing is a common way for cyber criminals to target individuals and organisations and can lead to sensitive information being compromised. DMARC can help prevent this by verifying where emails came from, and whether the location is genuine.
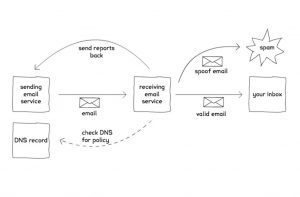
DMARC is an email standard that checks that emails came from the place they claim to. It does this using the sender policy framework (SPF) and DKIM discussed earlier.
DMARC helps organisations to:
- Protect their staff and customers from cyber crime
- Reduce costs associated with email fraud
- Improve trust in the emails that the organisation sends
- Monitor fraudulent use of their domains
Firstly, the SPF check confirms that the email came from a valid server, then it checks whether it was legitimately signed (the DKIM digital signature). DMARC also tells recipients what to do if an inbound email fails the DMARC checks and asks email services to send reports of where the email came from.
Some government organisations that use Office 365 are even going beyond the steps outlined above, and are adopting the E5 services such as ATP and safelinks, which provides an additional layer of protection.
Communicating changes to your organisation
It might be helpful to the people in your organisation if you communicate the changes that have been made. You can explain that this is a standard agreed across central government. Organisations who have implemented the changes are considered secure, so it is a positive move.
Core works with local and central government bodies and can help you secure your email to Official - Sensitive level. We have significant experience in helping customers implement the solutions outlined above, so contact us for a chat if this could help your organisation .