More and more, businesses of every kind are utilising cloud technologies to make them agile, future-proof and more productive. Microsoft’s cloud-based productivity suite, Microsoft 365, makes all these things happen and more.
Microsoft 365 combines Office 365, Enterprise Mobility + Security, and Windows 10, all in one package.
Two versions of Microsoft 365 are available: E3 and E5. Essentially, E3 and E5 are just different versions of the Microsoft 365 suite, with slightly different levels of functionality.
E5 has more features than E3, like PowerBI Pro, Teams telephony licensing (and most importantly for many businesses), additional security features - which is key to what this blog will discuss.
Having a secure environment is usually a top organisational priority, if not the top priority, when it comes to IT. Many businesses want to use cloud technologies but are afraid that their security will be compromised if they do; that isn’t the case.
In this blog, I look at the security features and functionality that come with the E5 version of Microsoft 365. Keep on reading to discover my top five security features and why they’re so useful.
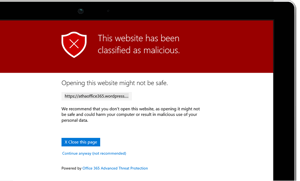
Office 365 Advanced Threat Protection
Office 365 Advanced Threat Protection (ATP) protects your organisation from phishing attacks. If an employee receives a malicious email with links and attachments, ATP will scan the links/attachments, and block them from being opened if they are identified as being suspicious. This is an integral part of protecting your IT environment; if an employee opens a malicious link or attachment your hard drive can be corrupted, your data stolen, and you can be exposed to all sorts of online and offline fraud. So, having ATP gives you the peace of mind that your network is protected even if a phishing email lands in your employees’ inbox.
You can also set anti-phishing policies, which require ATP to check incoming messages and depending on your policy, take action, like blocking or reporting the message if it is identified as a phishing attempt.
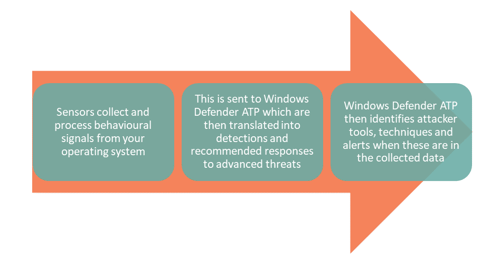
Windows Defender Advanced Threat Protection
Windows Defender ATP is a powerful product that is designed to help you detect and respond to security threats. Windows Defender ATP is embedded in Windows 10, so it provides an extra level of protection because it not only helps you detect threats to your operating system, but it also helps you understand the actions you can take to neutralise the threat. So, if your current setup means you don’t know whether you are getting threats or (if you are) how to respond to them, Windows Defender ATP is the tool to help you do that.
Microsoft Cloud App Security
Most people have heard of the term shadow IT. Shadow IT refers to IT applications that are managed and utilised without the knowledge of an organisation’s IT department. In some cases, the use of shadow IT in a business can’t be helped; but Microsoft have addressed the problem of shadow IT with Cloud App Security. Cloud App Security allows you to identify non-Microsoft cloud apps, and manage and secure them so that your organisation takes back control over the use of shadow IT. Resulting in less security risks within the business. You have control over who is accessing the applications, and there is further protection for any company data held within them.
As well as providing additional control, Cloud App Security protects sensitive information from being shared and used in the applications and protects against cyberthreats. So, if you have a lot of employees downloading and using non-Microsoft apps, Cloud App Security can give you peace of mind knowing that information is secure.
Office 365 Threat Intelligence
Detecting and intercepting security threats is a major priority for most businesses. Microsoft has a wealth of threat data and techniques to detect patterns that are synonymous with ‘attack behaviour’. Office 365 Threat Intelligence uses this knowledge to help you protect your networks and intercept security incidents. You are provided with an interactive tool that helps monitor, report and act on any security attacks Threat Intelligence detects.
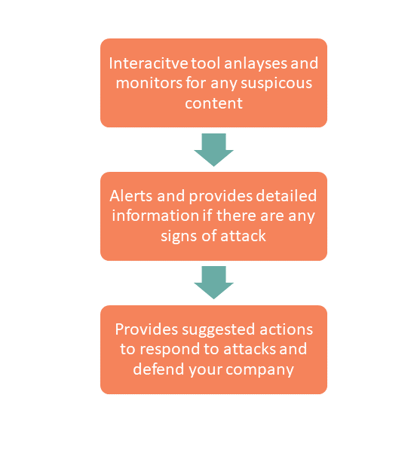
This is all in real-time so you can see any threats, and threats that have been stopped and blocked.
This is especially important for staying compliant with the GDPR. GDPR states that businesses are expected to demonstrate that they are applying appropriate technical measures to enable compliance, i.e., ensuring you have the right data protection software and policies in place. Threat Intelligence is a tool that helps create security policies to protect against malware and so helps organisations with compliance.
For Government agencies, there are minimum standards for cybersecurity. One of the main aspects of this is having a defined, planned and tested response to cybersecurity incidents that could impact sensitive information. Threat Intelligence includes the Attack Simulator, which allows departments to conduct realistic attack scenarios with the aim of creating a culture amongst staff of cybersecurity awareness and education.
Azure Information Protection P2
Azure Information Protection (AIP) is a great way to protect sensitive or confidential information and documents. AIP encrypts documents, tracks who has accessed a document and controls how it is shared, and who with.
For those familiar with Azure Information Protection, the P2 version is an extension of P1. It provides the ability to set automatic labels (like labelling a file as confidential if it contains sensitive data, such as credit card number) and control oversharing of information in Outlook.
For example, if I receive a document that is protected by AIP, I won’t be able to screenshot the document, save it or share my computer screen on Skype or Teams (thereby showing the document to someone else).
AIP is a great way to make sure that documents are controlled even when they leave your organisation.
If you need help deciding which licence is best for your business, get in touch with our Customer Success Manager, Kat, or for more information on our security services, ask about our security assessments.
Core also offer a Security Workshop for organisations that want to assess, review and improve their IT security landscape, or need help meeting industry standards and complying with regulations. Our experts will produce a comprehensive overview of your IT security and help you realise the value of Microsoft Security in your organisation. Book yours now.