Problem
Office 365 offers some fantastic benefits over traditional on-premise infrastructure. No costly infrastructure required, no advanced IT knowledge required, 100 GB mailbox, online meetings, document collaboration, 99.9 % uptime, flexibility allowing businesses to provide users with only the services they need and anytime and anywhere access to emails, documents, contacts, and calendars on any device.
This blog will explore the last benefit – anytime and anywhere access to Office 365.
As the image suggests, Office 365 means that we can all do our jobs from anywhere (coffee shop, pub, home) on any device we want to use. In reality, most companies do not work this way and do not want to work this way. For a lot of companies, Office 365 solves the problem of not requiring infrastructure, complicated exchange deployments and HA/DR as data is now in the cloud so is not the IT department's problem.
The ‘Anytime and Anywhere Access to Office 365’ does, however, highlight the following security concerns for Office 365 deployed with ‘out of the box’ settings.
- Office 365 can be accessed from anywhere – not just in the office, anywhere there is internet access.
- Office 365 can be accessed from any device – not just corporate owned devices, any device (Personal Windows/Mac laptop, tablet, phone, any device with a browser or Outlook client installed).
- Office 365 can be accessed by just a username and password.
From a data loss prevention point of view, this causes the following issues:
- Emails can be cached offline and copied elsewhere on a home PC with Outlook.
- Mail can be downloaded to mobile devices and copied to other locations.
- OneDrive for Business can be synced offline to a home PC and all data copied elsewhere/shared.
- SharePoint Online can be synced offline to a home PC and all data copied elsewhere/shared.
- Multi-factor is not turned on by default for Office 365 – To login only a username and password is required.
I always highlight this issue during my first workshop with a new client about to move some services to Office 365. Some clients accept this behaviour as being the new flexible working world, most clients do not; and I can see the Security Manager fall off their chair about moving services to the cloud!
The old solution to these issues with on-premise environments used to be VPNs. VPNs control who can and cannot connect to on-premise data. However, once we start moving data/resources into the cloud, we need to implement different solutions to control access to our data.
The majority of requests for lock down of Office 365 are as follows:
- Can we lock down access to Office 365 to our company offices?
- Can we lock down access to Office 365 to our corporate devices?
- Can we provide additional security during login process – i.e., MFA?
The answer to these security questions is yes: Azure offers Conditional Access to lock down Office 365. However, as with most things in life, it will cost you a bit extra. For this additional service, each user will need an Azure AD Premium license which also comes bundled in Enterprise Mobility and Security Suite – nothing comes for free.
Solution
Microsoft introduced Conditional Access to resolve this problem. Conditional Access allows administrators to control what Office 365 apps users can gain access to based on if they pass/fail certain conditions.
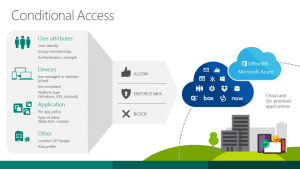
These conditions are enforced by building a policy (or multiple policies) to control how users access your Office 365 resources.
Policy Conditions
The following conditions can be controlled by the policy:
- Users/Groups – What users do you want to control – Users can be included/excluded from the policy if required. You will always get the person who is too important for this policy and wants to access everything from their personal iPad. It also allows you to test policies before rolling out to the wider business avoiding locking everyone out!
- Cloud Apps- What apps do you want to control? Conditional Access does not need to apply to all of Office 365, you can be more granular and just control access to specific apps – E.g. Exchange Online.
- Client App – Control what app/software the user is connecting from to the data – E.g. allow browsers but disable mobile and desktop Outlook apps.
- Device Platform – Control what devices users can connect from – E.g. allow Windows and iOS but block Android phones.
- Location – Control what IPs can connect to Office 365 – E.g. could limit this to the office external IP.
- Sign In Risk – Control signs in if Office 365/Azure thinks the sign in is not coming from the genuine user – E.g. if someone signs in from London then New York 30 mins later.
Based on the conditions above, access can be allowed to Office 365 with the following conditions:
- Require multi-factor authentication– User is allowed in but will need to complete additional security to log in, e.g.:
- Phone call
- Text message
- Mobile app
- Require device to be marked as compliant – Device must be Intune compliant, E.g. the device must match the Intune compliance policies to be able to connect.
- Require domain joined (Hybrid Azure AD) – Devices must be Hybrid Azure AD joined – E.g. Mobile Devices Azure AD registered and domain joined machines are set to automatically register in their Azure AD.
- Require approved app – You can select the requirement to grant access only if a connection attempt was made by an approved client app. These apps support Mobile Application Management (MAM) policies, so administrators can wrap security around these apps (e.g. stop copying and pasting information out of these apps).
User Experience for requirements
The above settings offer a wide range of options for restricting access to Office 365. Let's take our three most common requests and show the user experience if they try and access Office 365 from non-compliant devices:
- Can we lock down access to Office 365 to our company offices?
- Can we lock down access to Office 365 to our corporate devices?
- Can we provide additional security during log on process – i.e. MFA?
Can we lock down access to Office 365 to our company offices?
For this example, we have restricted access so that users can only connect to Office 365 if they are coming from the corporate IP range (external).
| The following Settings were configured in Azure Conditional Access. | |
| Block access to Exchange Online based on location. | 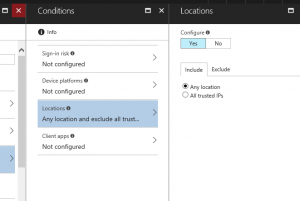 |
| The following screen details the end user experience for a user accessing Office 365 from a device that is not coming from the corporate IP address. | |
| User logs into Office 365 with credentials. | 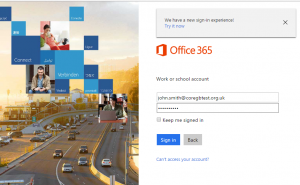 |
| Azure Conditional Access identifies that the user is not coming from a trusted IP address and blocks access. | 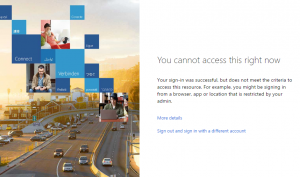 |
Can we lock down access to Office 365 to our corporate devices?
For this example, we have restricted access so that users can only connect to Office 365 if they are on a domain-joined device or mobile device that has been enrolled in Intune/Azure AD. Below is the user experience if a user is on a non-domain joined machine:
| The following settings were configured in Azure Conditional Access. | |
| Allow access to Exchange Online based on device – I.e. only allow if a device is domain joined and registered in Azure AD. | 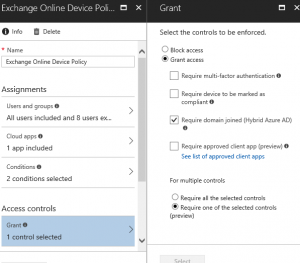 |
| The following screen details the end user experience for a user accessing Office 365 from a non-domain joined machine. | |
| User logs into Office 365 with credentials. | 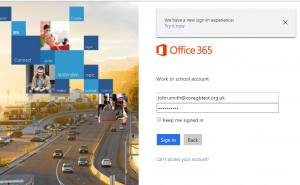 |
| Azure Conditional Access identifies that the user is not coming from a domain joined machine and refuses the connection – The following screen shows the OWA experience. | 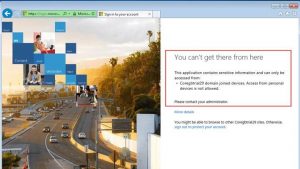 |
| Azure Conditional Access identifies that the user is not coming from a domain joined machine and refuses the connection – The following screen shows the Outlook 2016 experience. | 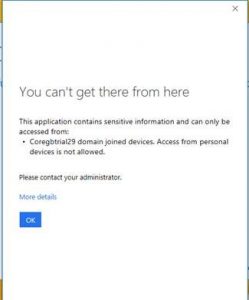 |
Can we provide additional security during log on process – i.e. MFA?
For this example, we have configured additional security for users accessing Office 365 if they are NOT coming from the corporate IP range (external). Please note, MFA only provides additional security if the user has the correct MFA devices they can log in to Office 365 from any device.
| The following settings were configured in Azure Conditional Access. | |
| Require additional security to Office 365 if accessing from non-corporate IP range. | 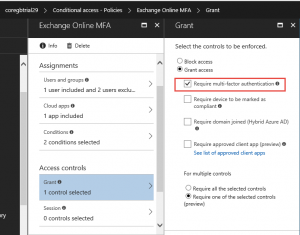 |
| The following screen details the end user experience for a user accessing Office 365 from a device that is not coming from the corporate IP address. | |
| User logs into Office 365 with credentials. | 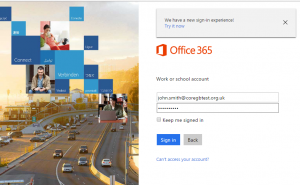 |
| Azure Conditional Access identifies that the user is not coming from a trusted IP address requires additional security. | 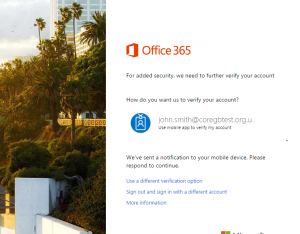 |
| The user will need to approve additional security on their phone – e.g. Azure Authenticator App. | 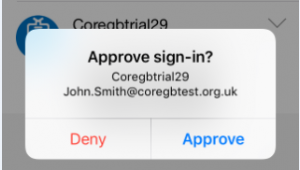 |
Gotchas
As with most Microsoft solutions, Conditional Access is not without its flaws.
Conditional Access will not work in the following situations:
- Client App – Not all client apps support Conditional Access – the Client App needs to support Modern Authentication. e.g. Outlook 2016 or Outlook 2013 (with a reg key change).
- Outlook 2010 will not work with Conditional Access and the user will be allowed to connect in; to lock down Outlook 2010 based on IP Ranges requires ADFS claims rules.
- Upgrade to Outlook 2016 if your business is still using this; it is 2018! Any 3rd party apps (e.g. Outlook Plugins) that don’t support above Outlook 2010, put pressure on the vendor to fix this. Don’t let your Office 365 migration be hindered by a non-future-proof app.
If your organisation is thinking about your IT security, and how it can be improved, why not book a Security Workshop from Core? Our experts will assess and review your current security landscape, helping you to address and solve challenges, optimising the security of your IT and helping you comply with industry standards and regulations.
Our comprehensive overview will give you the knowledge and insight you need to create an IT security strategy that fits your business needs and helps you to be completely secure using tools like Microsoft Security and Microsoft 365 to stay agile.
Microsoft Funded Workshops
We find the two biggest hurdles our customers face when adopting cloud solutions and cloud security, are disruption to a live environment, and gaining stakeholder buy in during uncertain times.
Our range of immersive workshops have designed with these obstacles in mind. We'll demonstrate the benefits of our cloud solutions to your decision-makers, and we'll even offer you the opportunity to develop a deployment plan to mitigate the risk.
If you're looking to modernise your workplace, and need help making the decision, our workshops are just what you need. Click the link below to see our range of immersive experiences, and take that first step towards your goal.









