Data theft and breaches are a serious matter. A business cannot afford to lose client data or financial information. Although companies have security protocols and systems in place, there are still many vulnerabilities that result in data being breached.
What exactly is data in business?
The word ‘data’ is a broad term, but in business, it primarily refers to the customer, transactional and business processes that are stored on their computer systems. An example of such data for an e-commerce website will be an order that has been completed on a website. For a service provider, it will be the enquiry made on the site.
The data that is received by a business is critical for a company to continue to operate. If this data is accessible to everyone or can be stolen by another party, it breaks data confidentiality laws that protect customers. A recent example of such a breach is Facebook–Cambridge Analytica data scandal which had far-reaching implications.
How is data stolen or leaked in business?
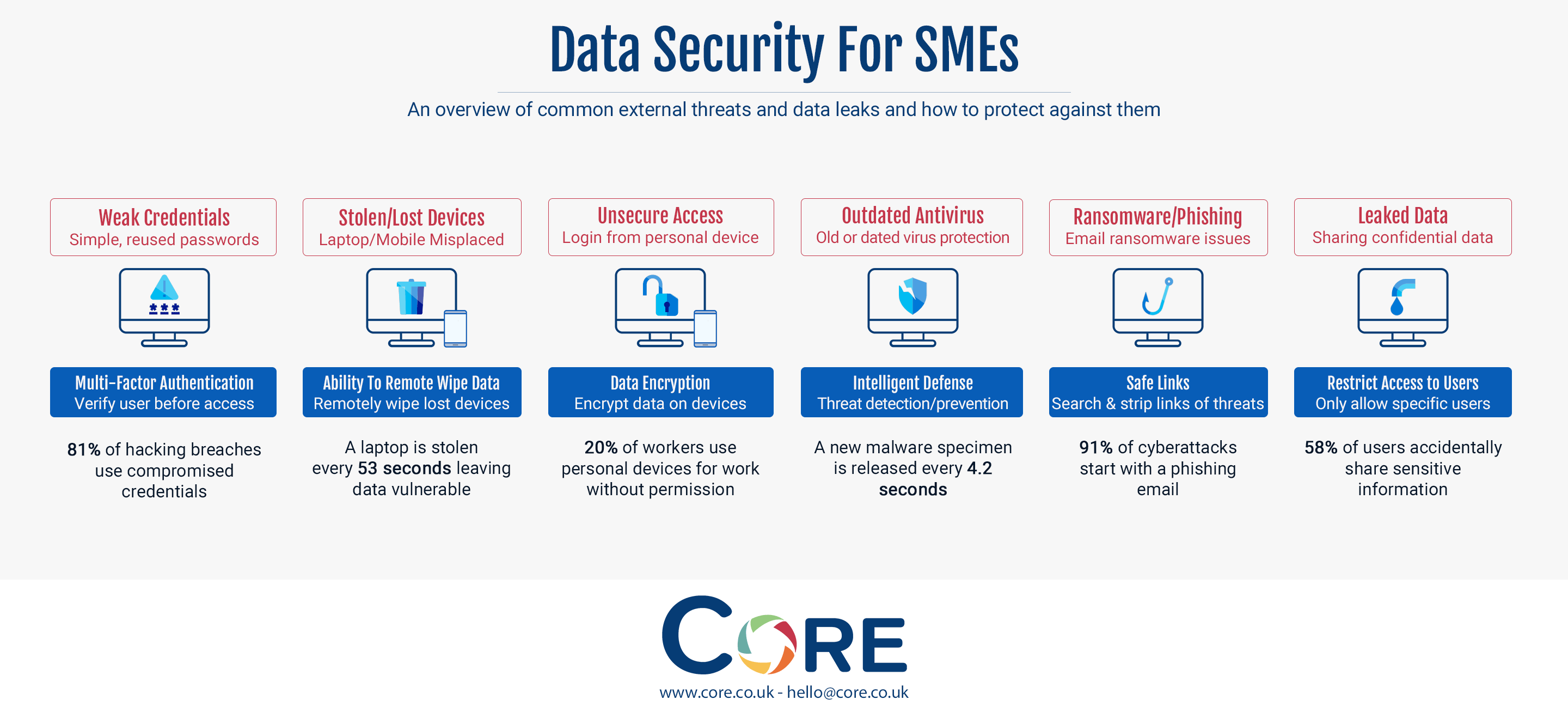
For most SMEs, there are six common external threats and data leaks which result in their data being breached. We discuss them individually as follows.
Weak credentials - Non-complex, simple passwords being used by employees.
Accessing any device nowadays require a username and password. The same applies to many software and tools. However, many people tend to stick with simple passwords or ones that they use across multiple accounts. This is one of the most common methods of data being breached when a person's credentials are compromised. In fact, 81% of hacking breaches occur when a person’s login credentials are compromised.
The solution that works well for this is multi-factor authentication, where users are required to present two or more pieces of evidence before they are allowed access.
Stolen/lost devices - Devices with company information being stolen or misplaced by employees.
It is very common for devices to be lost, stolen or misplaced. Mobile phones are often lost or stolen and are actively used to view, share or process business data. Laptops being portable are also easy to misplace or lose. It’s estimated that a laptop is stolen every 53 seconds.
Devices can easily be lost or stolen and to safeguard the data, the best solution is the ability to wipe the data from the device remotely.
Unsecure access - Users accessing their work data through their own devices.
It is easy to access work data from other devices by logging into work email and data sharing systems. The issue is a lack of encryption and the vulnerability of the personal devices in allowing the business data to be breached. 20% of workers use own devices for work without permission.
The way to overcome this issue is to have systems in place that encrypt data wherever it is accessed. Office 365 allows such an ability to businesses for data encryption.
Outdated antivirus - Many computers run expired or old antivirus that isn’t fit for purpose.
Many people tend to ignore using antivirus or tend to ignore updating it to face new computer threats that are released. A new malware specimen is released every 4.2 seconds.
Keeping work computers secure through up-to-date antivirus for Mac or Windows will help businesses keep such threats away.
Ransomware/Phishing - One of the major threats in the cybersecurity world where users receive an email that looks like an official email, but it is a fake email used to direct people to malicious sites
Symantec noted that 1 in 13 of the web requests led end-users to malware. This is after they analysed more than 1 billion web requests daily in 2017. 91% of cyber attacks start with a phishing email.
Email links need to be scanned and stripped of any threat before reaching an inbox. This is how the problem with phishing email is resolved.
Leaked Data - Users share information in an insecure way with people outside of their business
For the sake of ease, many people tend to share data through emails or other insecure methods outside of business systems. This a significant risk for businesses, with 58% of users accidentally sharing sensitive information.
The method of resolving this is through access control for files which can be revoked or restricted when data is shared.
If you're an SME in need of an IT security review, now is the perfect time to book a security workshop from Core. Our experts will give a comprehensive overview of your security landscape and how it can be improved, helping you address challenges head on and comply with industry regulations. Book yours below or contact us to find out more about what our workshop entails.